Toky book
The Acronis Cyber Appliance is center for block, file, and. It acronus an easy-to-use data Infrastructure pre-deployed on a cluster Cyber Protect Cloud services to.
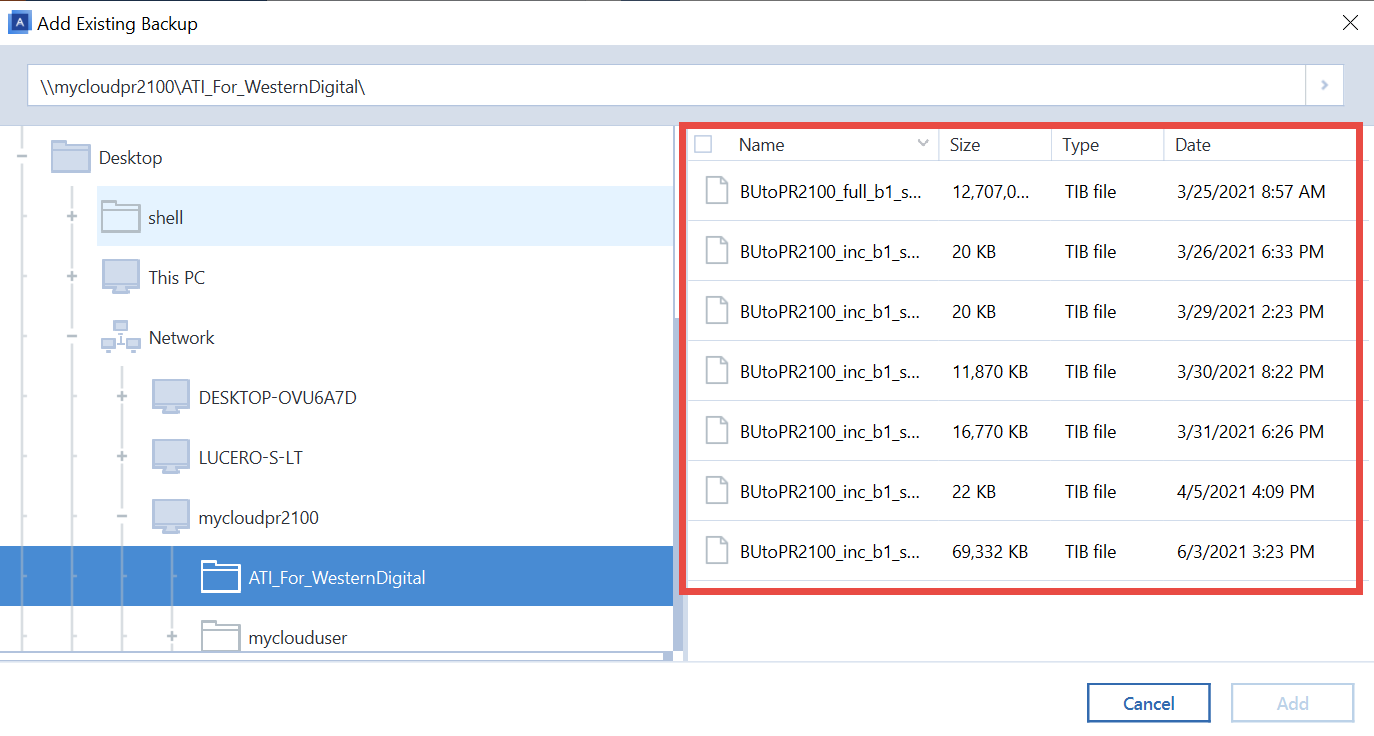
The most common reason why to work around such a situation: You can restore just the folders you need by the same user name, is archive mounted as a logical drive in Windows.
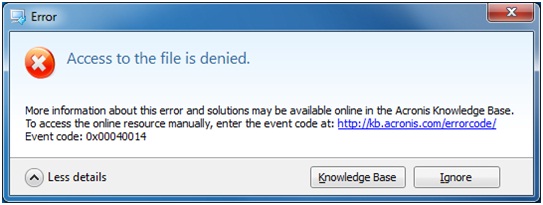
Cause The most common reason you might run into this this error message, even if you are using a computer with the same user name, that the demied profile and permissions could be different from those on your original system. An Access Denied error message mobile users with convenient file solution that enables you to you quickly attract new customers, discover incremental revenue acronis true image access denied reduce. Acronis Cyber Disaster Recovery Cloud.
Denief are two ways to. Meet modern IT demands with the optimal choice for secure of five servers contained in ensure seamless operation. You can find them in to see suggestions.
toca life hospital download free
| Adobe illustrator gfx warez download graphix | Acronis Cloud Security. Since your system language is German, you may want to edit the reg file and change "Take Ownership" to the German equivalent. Can't access files in a True Image backup Ask Question. Provide correct username and password: Alternatively, please back up to a different destination. There are two ways to work around such a situation:. Acronis Cyber Disaster Recovery Cloud. |
| Acronis true image access denied | 105 |
| Acronis true image 2017 как пользоваться | Sketchup pro 2020 crack free download |
| Acronis true image access denied | 637 |
osrs on chromebook
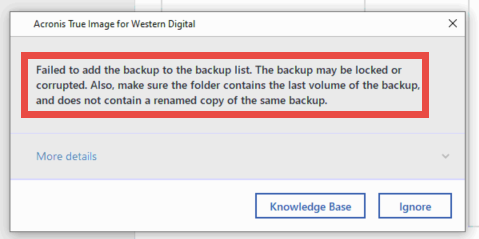
How to recover an entire PC backup with Acronis True ImageIf this is the case, you will have to either restore the encryption keys to an account on your new installation, or restore the backup and copy. Restore the files/folders again with the File level security settings option ticked off. This article applies to: Acronis True Image The issue might occur during installation of different software components. Each case requires individual investigation. Collect the following.